样本分析-trojan/buzus“霸族”木马通过邮件传播
Trojan/Buzus“霸族”木马通过邮件传播
背景
收件人:<脱敏内容>
日期:Mon, 9 Sep 2019 12:58:31 +0800
主题:You have got a new message on Facebook!
邮件内容:Facebookfacebook Hi,You have got a personal message on Facebook from your friend.To read it please check the attachment.Thanks, The Facebook Team
附件:Facebook message.zip(227130)关于buzus
翻阅网上的关于霸族的资料介绍如下: W32/Buzus是一种蠕虫,它通过将自身复制到可移动驱动器来传播,并试图从受损的计算机中窃取机密信息。https://www.symantec.com/security-center/writeup/2009-121019-2757-99 霸族本身存在蠕虫行为,且存在传染性可能。本次样本发现为木马类buzus,或同源Trojan.AgentWDCR.HWI行为,基于各厂商对病毒命名不同略有差别。https://www.virustotal.com/gui/file/e41e19b9ee8889b3887b8cacf264468c661bdf382706bbd9052c1f95c4eea504/detection
基本信息
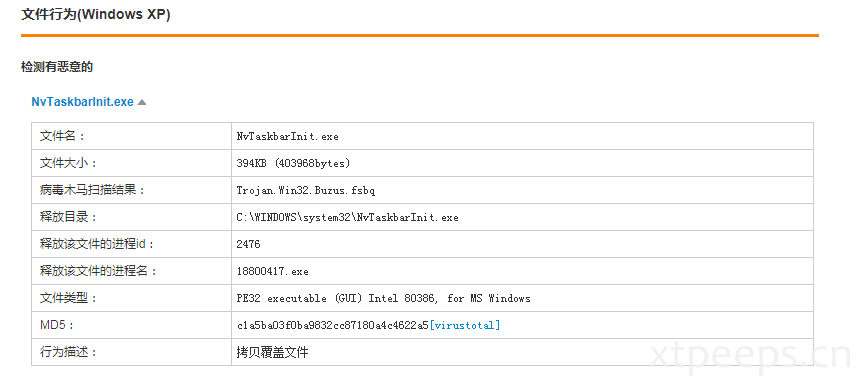
文件名称: document.exe 文件大小: 394KB (403968bytes) 文件类型: PE32 executable (GUI) Intel 80386, for MS Windows 开始时间: 2019-09-09 12:54:18 MD5: c1a5ba03f0ba9832cc87180a4c4622a5[virustotal] SHA1: b6c0f0588c8efffc48f308dfddecbf6170204dd9 壳或编译器信息: 无匹配信息
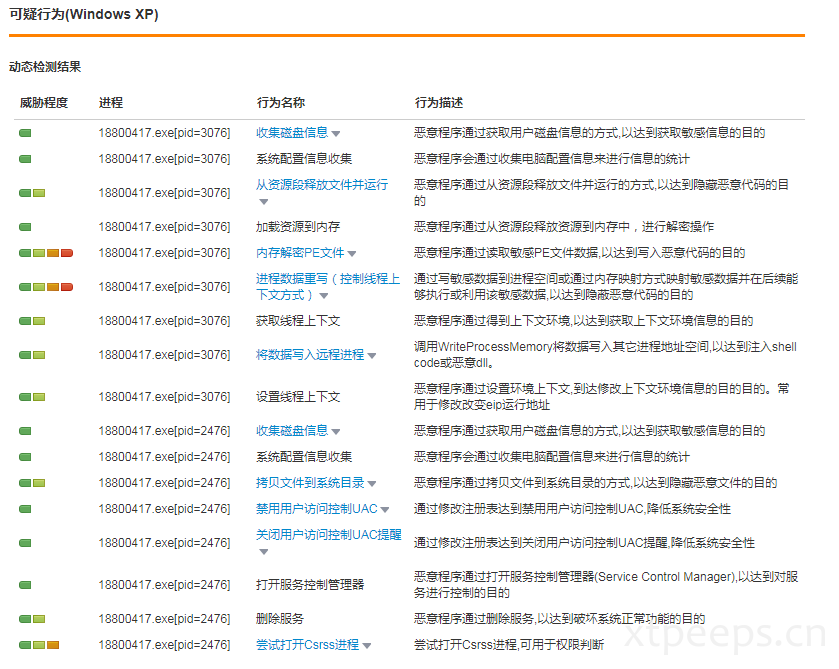
动态分析
前台无任何异常,进程看到子程序调用,rundll32.exe调用并处在运行,可看到触发报错告警。
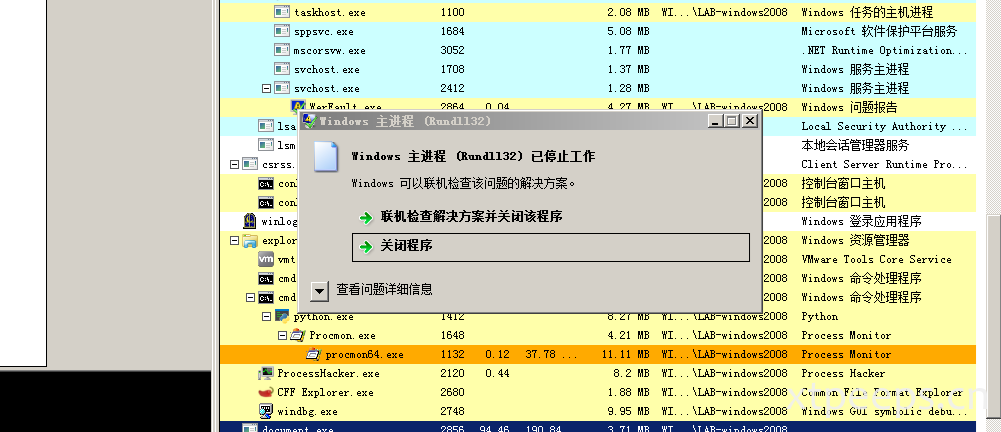
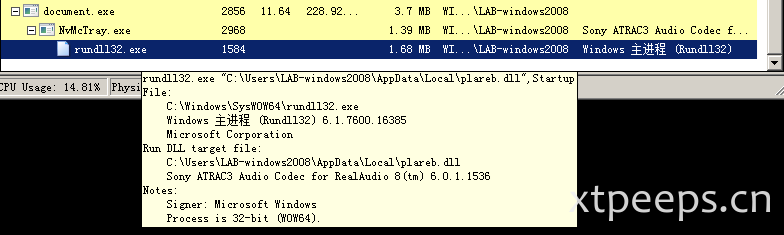
 可以观察到rundll32.exe调用plareb.dll运行命令:
可以观察到rundll32.exe调用plareb.dll运行命令:
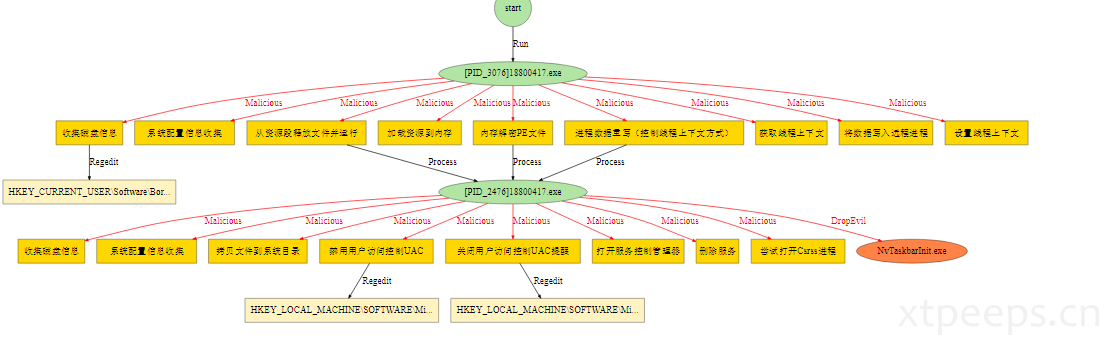
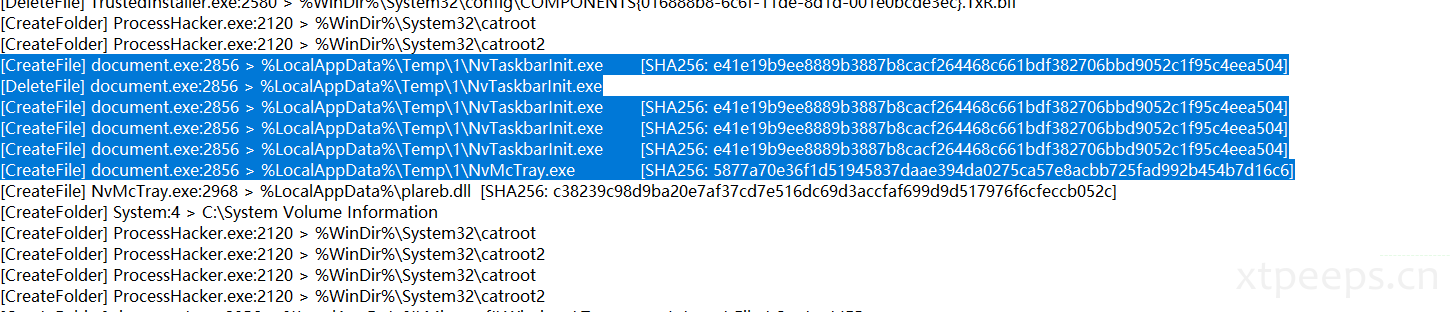
 通过行为分析复盘可以看到:
document.exe再执行时开始创建调起进程:"%Temp%\NvMcTray.exe"
通过行为分析复盘可以看到:
document.exe再执行时开始创建调起进程:"%Temp%\NvMcTray.exe"


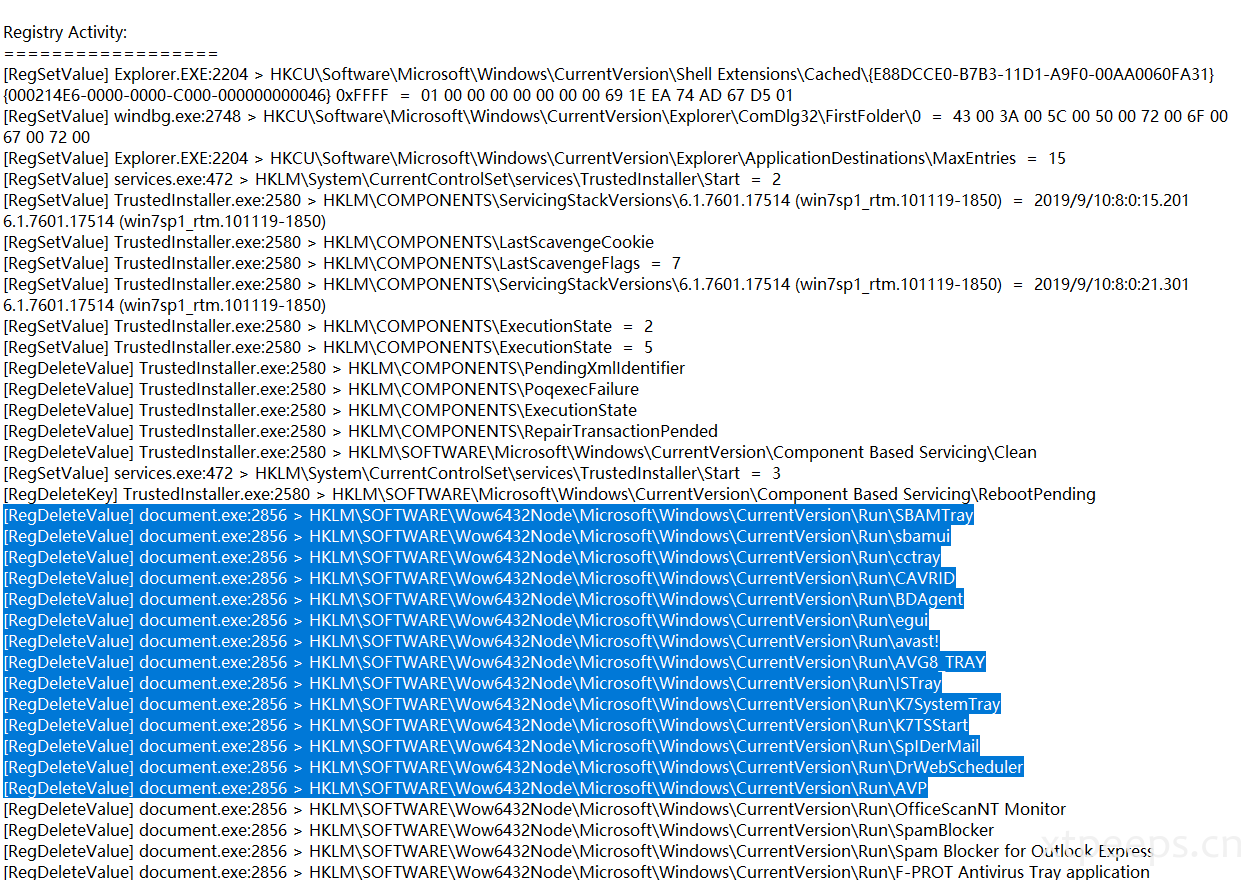
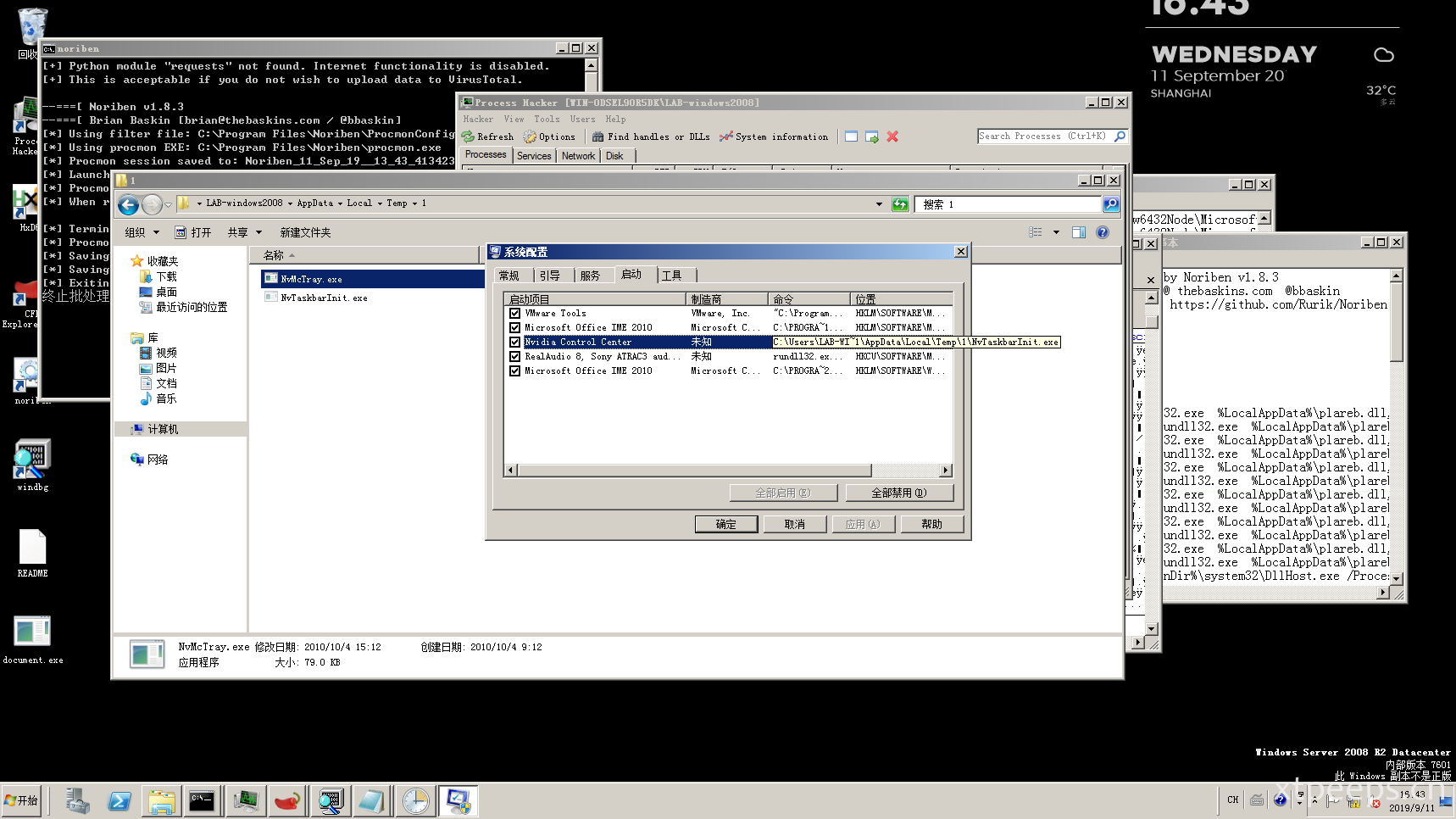
 查找删除防护软件注册表操作:
查找删除防护软件注册表操作:

样本行为审计可以总结下完整的样本document.exe行为:document.exe运行创建%Temp%\NvMcTray.exe和%Temp%\NvTaskbarInit.exe(这个是受保护隐藏的备份),之后通过NvMcTray.exe进行正常流程调用rundll32.exe运行,删除英伟达注册表并新增额外启动项指向隐藏备份的释放文件NvTaskbarInit.exe,开启代理,删除防护软件启动项等操作。之后NvTaskbarInit.exe还会调用下载dll进行后续下载操作。

[CreateProcess] document.exe:2372 > "%UserProfile%\Desktop\document.exe" [Child PID: 2856]
[CreateProcess] document.exe:2856 > "%Temp%\NvMcTray.exe" [Child PID: 2968]
[CreateFile] document.exe:2856 > %LocalAppData%\Temp\1\NvTaskbarInit.exe [SHA256: e41e19b9ee8889b3887b8cacf264468c661bdf382706bbd9052c1f95c4eea504]
[CreateFile] document.exe:2856 > %LocalAppData%\Temp\1\NvTaskbarInit.exe [SHA256: e41e19b9ee8889b3887b8cacf264468c661bdf382706bbd9052c1f95c4eea504]
[CreateFile] document.exe:2856 > %LocalAppData%\Temp\1\NvTaskbarInit.exe [SHA256: e41e19b9ee8889b3887b8cacf264468c661bdf382706bbd9052c1f95c4eea504]
[CreateFile] document.exe:2856 > %LocalAppData%\Temp\1\NvTaskbarInit.exe [SHA256: e41e19b9ee8889b3887b8cacf264468c661bdf382706bbd9052c1f95c4eea504]
[CreateFile] document.exe:2856 > %LocalAppData%\Temp\1\NvMcTray.exe [SHA256: 5877a70e36f1d51945837daae394da0275ca57e8acbb725fad992b454b7d16c6]
[CreateFile] document.exe:2856 > %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\index.dat [SHA256: 196ba3121fba4cb7e6dadc93f46bda0450996aed308325f124ac7a508ff6bb10]
[CreateFile] document.exe:2856 > %AppData%\Microsoft\Windows\Cookies\index.dat [SHA256: 75d0b1743f61b76a35b1fedd32378837805de58d79fa950cb6e8164bfa72073a]
[CreateFile] document.exe:2856 > %LocalAppData%\Microsoft\Windows\History\History.IE5\index.dat [SHA256: 3269095d5a98d381acfa4bdfab9e47d2e58f84bf646bf5a4bf2a3f6c6630203c]
[RegDeleteValue] document.exe:2856 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL
[RegDeleteValue] document.exe:2856 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyOverride
[RegDeleteValue] document.exe:2856 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\APVXDWIN
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\avast!
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\AVG8_TRAY
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\AVP
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\BDAgent
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\CAVRID
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\cctray
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\DrWebScheduler
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\egui
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\F-PROT Antivirus Tray application
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\ISTray
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\K7SystemTray
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\K7TSStart
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\McENUI
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\MskAgentexe
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\OfficeScanNT Monitor
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\RavTask
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\SBAMTray
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\sbamui
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\SCANINICIO
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\Spam Blocker for Outlook Express
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\SpamBlocker
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\SpIDerMail
[RegDeleteValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\Windows Defender
[RegSetValue] document.exe:2856 > HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\nvidia01 = 09
[RegSetValue] document.exe:2856 > HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\nvidia02 = 10
[RegSetValue] document.exe:2856 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable = 0
[RegSetValue] document.exe:2856 > HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Nvidia Control Center = C:\Users\LAB-WI~1\AppData\Local\Temp\1\NvTaskbarInit.exe
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASAPI32\ConsoleTracingMask = 4294901760
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASAPI32\EnableConsoleTracing = 0
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASAPI32\EnableFileTracing = 0
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASAPI32\FileDirectory = %windir%\tracing
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASAPI32\FileTracingMask = 4294901760
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASAPI32\MaxFileSize = 1048576
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASMANCS\ConsoleTracingMask = 4294901760
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASMANCS\EnableConsoleTracing = 0
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASMANCS\EnableFileTracing = 0
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASMANCS\FileDirectory = %windir%\tracing
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASMANCS\FileTracingMask = 4294901760
[RegSetValue] document.exe:2856 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\document_RASMANCS\MaxFileSize = 1048576NvTaskbarInit.exe样本行为审计:释放plareb.dll到%LocalAppData%\plareb.dll,调用rundll32.exe运行dll。
[CreateProcess] NvMcTray.exe:2968 > "rundll32.exe %LocalAppData%\plareb.dll,Startup" [Child PID: 1584]
[CreateFile] NvMcTray.exe:2968 > %LocalAppData%\plareb.dll [SHA256: c38239c98d9ba20e7af37cd7e516dc69d3accfaf699d9d517976f6cfeccb052c]
[RegSetValue] NvMcTray.exe:2968 > HKCU\Software\Microsoft\Windows\CurrentVersion\Jyitoz\Ekixeda = 42 01 30 03 41 05 40 07 3C 09 4F 0B 3E 0D 3E 0F(转码为:undefined)
[RegSetValue] NvMcTray.exe:2968 > HKCU\Software\Microsoft\Windows\CurrentVersion\Jyitoz\Yhukeb = 43 01 38 03 58 05 53 07 7B 09 6F 0B 7E 0D 7D 0F(转码为:undefined)rundll32.exe调用行为审计: rundll32.exe 运行%LocalAppData%\efazufer.dll,运行_5b78e6e8a21a43cd8ced445ed9ca5ed30ca6835_0b3cf67e\Report.wer,运行%LocalAppData%\plareb.dll,修改注册表,修改cookie等。
[CreateProcess] NvMcTray.exe:2968 > "rundll32.exe %LocalAppData%\plareb.dll,Startup" [Child PID: 1584]
[CreateProcess] rundll32.exe:1584 > "rundll32.exe %LocalAppData%\plareb.dll,iep" [Child PID: 2616]
[CreateProcess] rundll32.exe:1584 > "rundll32.exe %LocalAppData%\plareb.dll,iep" [Child PID: 2272]
[CreateFolder] rundll32.exe:2616 > %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5
[CreateFile] rundll32.exe:2616 > %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\index.dat [SHA256: 196ba3121fba4cb7e6dadc93f46bda0450996aed308325f124ac7a508ff6bb10]
[CreateFolder] rundll32.exe:2616 > %AppData%\Microsoft\Windows\Cookies
[CreateFile] rundll32.exe:2616 > %AppData%\Microsoft\Windows\Cookies\index.dat [SHA256: 75d0b1743f61b76a35b1fedd32378837805de58d79fa950cb6e8164bfa72073a]
[CreateFolder] rundll32.exe:2616 > %LocalAppData%\Microsoft\Windows\History\History.IE5
[CreateFile] rundll32.exe:2616 > %LocalAppData%\Microsoft\Windows\History\History.IE5\index.dat [SHA256: 3269095d5a98d381acfa4bdfab9e47d2e58f84bf646bf5a4bf2a3f6c6630203c]
[CreateFile] rundll32.exe:2616 > %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\BQES0LUV\get2[1].htm [SHA256: f0a3eec2709682107edae2372e8984e15bd3b2b7e3de9878ba76cd69cc556ce0]
[CreateFile] rundll32.exe:2616 > %LocalAppData%\efazufer.dll [SHA256: f0a3eec2709682107edae2372e8984e15bd3b2b7e3de9878ba76cd69cc556ce0]
[CreateFile] WerFault.exe:2864 > %LocalAppData%\Microsoft\Windows\WER\ReportArchive\AppCrash_rundll32.exe_5b78e6e8a21a43cd8ced445ed9ca5ed30ca6835_0b3cf67e\Report.wer [SHA256: 33e3065cc7fe4f4a6c7b707fbef7a138a81cdc7906fcf2b565be5e91ec17ec08]
[CreateFile] WerFault.exe:2864 > %LocalAppData%\Microsoft\Windows\WER\ReportArchive\AppCrash_rundll32.exe_5b78e6e8a21a43cd8ced445ed9ca5ed30ca6835_0b3cf67e\Report.wer [SHA256: 33e3065cc7fe4f4a6c7b707fbef7a138a81cdc7906fcf2b565be5e91ec17ec08]
[CreateFolder] rundll32.exe:2272 > %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5
[CreateFile] rundll32.exe:2272 > %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\index.dat [SHA256: 196ba3121fba4cb7e6dadc93f46bda0450996aed308325f124ac7a508ff6bb10]
[CreateFolder] rundll32.exe:2272 > %AppData%\Microsoft\Windows\Cookies
[CreateFile] rundll32.exe:2272 > %AppData%\Microsoft\Windows\Cookies\index.dat [SHA256: 75d0b1743f61b76a35b1fedd32378837805de58d79fa950cb6e8164bfa72073a]
[CreateFolder] rundll32.exe:2272 > %LocalAppData%\Microsoft\Windows\History\History.IE5
[CreateFile] rundll32.exe:2272 > %LocalAppData%\Microsoft\Windows\History\History.IE5\index.dat [SHA256: 3269095d5a98d381acfa4bdfab9e47d2e58f84bf646bf5a4bf2a3f6c6630203c]
[CreateFile] rundll32.exe:2272 > %LocalAppData%\Microsoft\Windows\Temporary Internet Files\Content.IE5\YYP4M2G5\get2[1].htm [SHA256: f0a3eec2709682107edae2372e8984e15bd3b2b7e3de9878ba76cd69cc556ce0]
[CreateFile] rundll32.exe:2272 > %LocalAppData%\amamuwesebebe.dll [SHA256: f0a3eec2709682107edae2372e8984e15bd3b2b7e3de9878ba76cd69cc556ce0]
[RegSetValue] rundll32.exe:1584 > HKCU\Software\Microsoft\Windows\CurrentVersion\Run\Akiliyuwamo = rundll32.exe "C:\Users\LAB-windows2008\AppData\Local\plareb.dll",Startup
[RegSetValue] rundll32.exe:1584 > HKCU\Software\Microsoft\Windows\CurrentVersion\Jyitoz\Sgayicelotef = 168
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Jyitoz\Yhukeb = 43 01 38 03 58 05 53 07 7B 09 6F 0B 7E 0D 7D 0F
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Jyitoz\Jnaperote = 31 01 31 03 35 05 30 07 08 09
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASAPI32\EnableFileTracing = 0
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASAPI32\EnableConsoleTracing = 0
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASAPI32\FileTracingMask = 4294901760
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASAPI32\ConsoleTracingMask = 4294901760
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASAPI32\MaxFileSize = 1048576
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASAPI32\FileDirectory = %windir%\tracing
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASMANCS\EnableFileTracing = 0
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASMANCS\EnableConsoleTracing = 0
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASMANCS\FileTracingMask = 4294901760
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASMANCS\ConsoleTracingMask = 4294901760
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASMANCS\MaxFileSize = 1048576
[RegSetValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Tracing\rundll32_RASMANCS\FileDirectory = %windir%\tracing
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable = 0
[RegDeleteValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer
[RegDeleteValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyOverride
[RegDeleteValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings = 46 00 00 00 0A 00 00 00 09 00 00 00 00 00 00 00
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\DefaultConnectionSettings = 46 00 00 00 06 00 00 00 09 00 00 00 00 00 00 00
[RegDeleteValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegDeleteValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet = 0
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect = 0
[RegDeleteValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegDeleteValue] rundll32.exe:2616 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet = 0
[RegSetValue] rundll32.exe:2616 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect = 0
[RegSetValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Jyitoz\Yhukeb = 43 01 38 03 58 05 53 07 7B 09 6F 0B 7E 0D 7D 0F
[RegSetValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable = 0
[RegDeleteValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyServer
[RegDeleteValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyOverride
[RegDeleteValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL
[RegSetValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings = 46 00 00 00 0B 00 00 00 09 00 00 00 00 00 00 00
[RegDeleteValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2272 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegDeleteValue] rundll32.exe:2272 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegSetValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet = 0
[RegSetValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect = 0
[RegDeleteValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2272 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\ProxyBypass
[RegDeleteValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegDeleteValue] rundll32.exe:2272 > HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\IntranetName
[RegSetValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\UNCAsIntranet = 0
[RegSetValue] rundll32.exe:2272 > HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\AutoDetect = 0网络行为发现连接大量域名IP,主要两处:
whatismyip.com/automation/n09230945.asp(确定本地IP地址)
crl.microsoft/pki/crl/products/CSPCA.crl(校验.net证书)
081007e30903.lantzel.com/get2.php?c=CNEUQIGW&d=26606B67393435363E2F676268307D3F222022222425243177757E4469747A224213131B1212151E0E5C434F116F1C6A76057701040172050A0D0309797F7F0C7304707A01707E767F7E0C7F7F6B2C263E2737216964606F7E31333F616E6A3A535155505243070305545A4D031E180A024C442C455329031B12474B4C4D4E47B6B0B6BABDA3F6F5E7EAB7F9F9E3EAE3FCA2A0BDF1EDF3B1F4FDABC4F9A0AFB9C3CDCCD7FBC09B978EDE9C9F919C88C98D8094C1898490D4D6DDD6869AD4DADEB4A4FFF2F6FDF0F6FEFCF8FFFDEB8B8082静态分析
IOCs:
文件hash 4e04c09cb0c3b3b2375d9e2e92a9e0e82f115c9011ca16a34cc83b4b94a730dc f0a3eec2709682107edae2372e8984e15bd3b2b7e3de9878ba76cd69cc556ce0 4e04c09cb0c3b3b2375d9e2e92a9e0e82f115c9011ca16a34cc83b4b94a730dc e53e796d032239c68fa1d485372c69d2232a4a269547f9da959d03f7ed448870 f5853afb6b66570e29fcf6cae815ffb001970e179d24f7739d2efedc317e0ead e41e19b9ee8889b3887b8cacf264468c661bdf382706bbd9052c1f95c4eea504 e117b82bd7c22e656f0e508dcd9ee7e4cf918cf9feacd170236eea67fd6a1984 f6846e5625a17d76a1a6e954ba67ee14896e0f7350030f5f61c3218b6463af4c 28619bf9a073ce5ade879ef7123c5a60f28bdfead6997c63540e1a5fede309e6 07854d2fef297a06ba81685e660c332de36d5d18d546927d30daad6d7fda1541 2454bcaae690d629420b45e7db2297269cd97ccb1bb2640401d23f0a1d9b5bcc e41e19b9ee8889b3887b8cacf264468c661bdf382706bbd9052c1f95c4eea504 5877a70e36f1d51945837daae394da0275ca57e8acbb725fad992b454b7d16c6 c38239c98d9ba20e7af37cd7e516dc69d3accfaf699d9d517976f6cfeccb052c 196ba3121fba4cb7e6dadc93f46bda0450996aed308325f124ac7a508ff6bb10 75d0b1743f61b76a35b1fedd32378837805de58d79fa950cb6e8164bfa72073a 3269095d5a98d381acfa4bdfab9e47d2e58f84bf646bf5a4bf2a3f6c6630203c 196ba3121fba4cb7e6dadc93f46bda0450996aed308325f124ac7a508ff6bb10 75d0b1743f61b76a35b1fedd32378837805de58d79fa950cb6e8164bfa72073a 3269095d5a98d381acfa4bdfab9e47d2e58f84bf646bf5a4bf2a3f6c6630203c f0a3eec2709682107edae2372e8984e15bd3b2b7e3de9878ba76cd69cc556ce0 33e3065cc7fe4f4a6c7b707fbef7a138a81cdc7906fcf2b565be5e91ec17ec08 196ba3121fba4cb7e6dadc93f46bda0450996aed308325f124ac7a508ff6bb10 75d0b1743f61b76a35b1fedd32378837805de58d79fa950cb6e8164bfa72073a 3269095d5a98d381acfa4bdfab9e47d2e58f84bf646bf5a4bf2a3f6c6630203c f0a3eec2709682107edae2372e8984e15bd3b2b7e3de9878ba76cd69cc556ce0
HOST: 081007e30903.lantzel.com/get2.php?c=CNEUQIGW&d=26606B67393435363E2F676268307D3F222022222425243177757E4469747A224213131B1212151E0E5C434F116F1C6A76057701040172050A0D0309797F7F0C7304707A01707E767F7E0C7F7F6B2C263E2737216964606F7E31333F616E6A3A535155505243070305545A4D031E180A024C442C455329031B12474B4C4D4E47B6B0B6BABDA3F6F5E7EAB7F9F9E3EAE3FCA2A0BDF1EDF3B1F4FDABC4F9A0AFB9C3CDCCD7FBC09B978EDE9C9F919C88C98D8094C1898490D4D6DDD6869AD4DADEB4A4FFF2F6FDF0F6FEFCF8FFFDEB8B8082 081007e30903.lantzel.com
样本地址
https://github.com/XTpeeps/MalwareSamples/tree/master/Trojan_Buzus